Malware
MSI Hacked by Money Message Ransomware Group, Demands $4 Million as Ransom
Money Message, a ransomware gang, has claimed to have breached the computer hardware giant MSI’s systems and demanded a ransom of $4 million. The gang has threatened to release sensitive data, including financial information and source code, if MSI fails to pay the ransom. The company has not confirmed the breach yet, but the incident highlights the growing threat of ransomware attacks on businesses.

MSI listed on “Money Message” Ransomware Gang’s Extortion Site
Global hardware giant MSI (Micro-Star International), headquartered in Taiwan, has been listed on the extortion portal of a new ransomware gang known as “Money Message.” The gang claims to have stolen source code from MSI’s network and has threatened to publish all these allegedly stolen documents in about five days unless MSI meets its ransom payment demands.
MSI is a leading manufacturer of motherboards, graphics cards, desktops, laptops, servers, industrial systems, PC peripherals, and infotainment products, with an annual revenue that surpasses $6.5 billion.
The threat actor has listed MSI on its data leak website and posted screenshots of what they claim to be the hardware vendor’s CTMS and ERP databases and files containing software source code, private keys, and BIOS firmware.
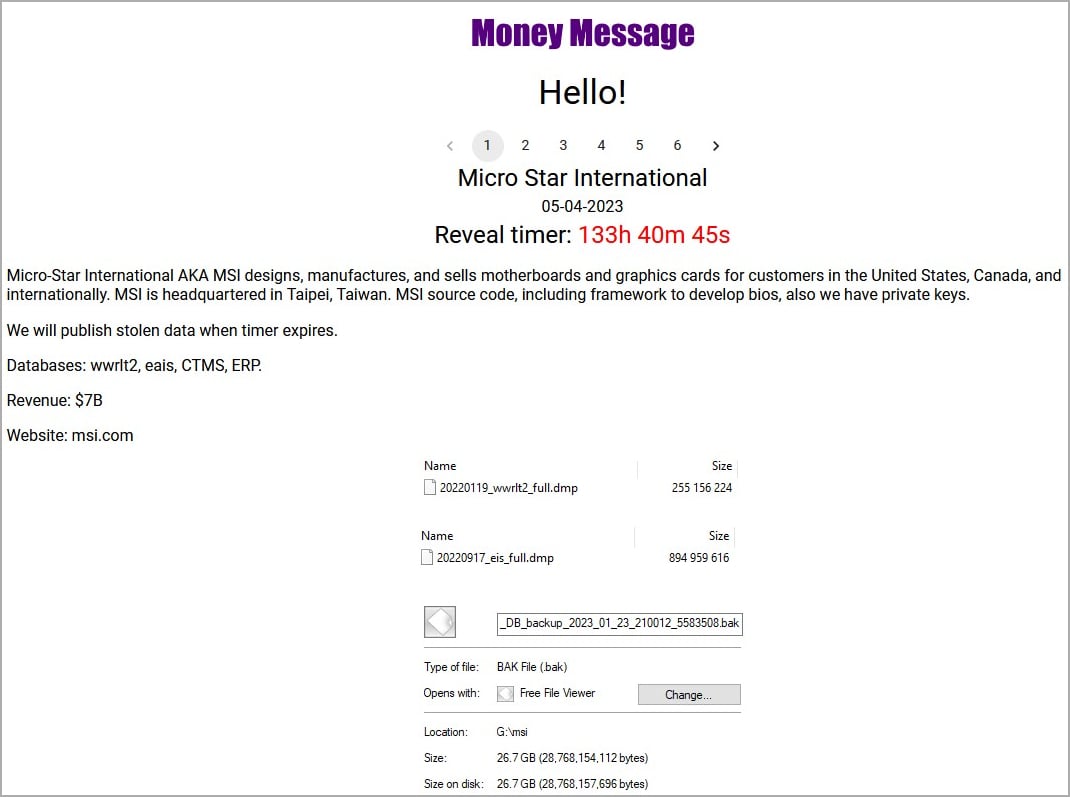
According to a report by IT Services, Money Message is a novel ransomware group that has been active recently and has attacked a well-known computer hardware vendor. The threat actors claimed to have stolen 1.5TB of data from MSI’s systems, including source code and databases, and demanded a ransom payment of $4,000,000.
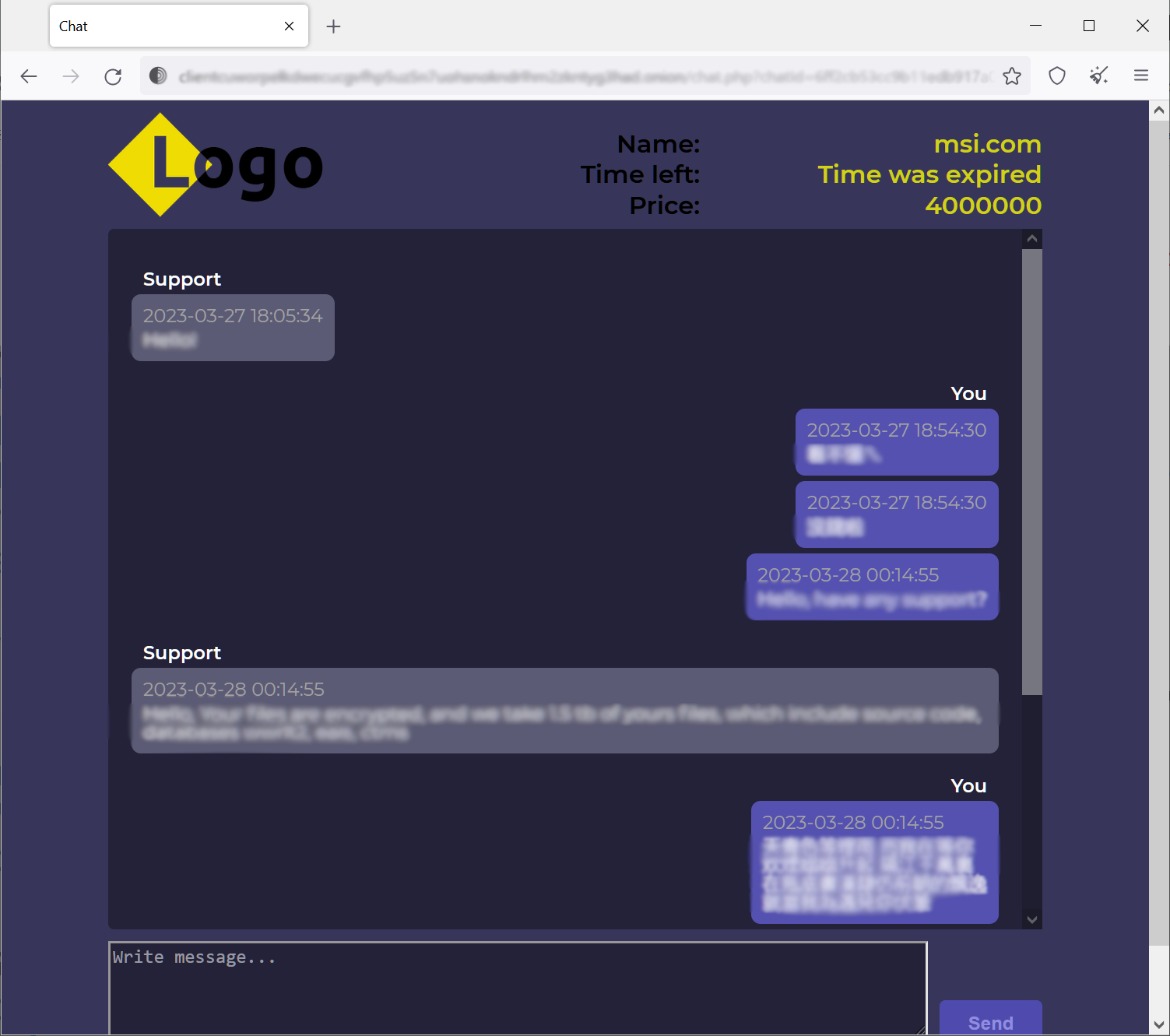
During a chat with an MSI agent, a Money Message operator said, “Say your manager, that we have MSI source code, including the framework to develop BIOS, also we have private keys able to sign in any custom module of those BIOS and install it on PC with this BIOS.”
IT Services has reached out to MSI for comment but has not yet received a response. As such, the validity of Money Message’s data breach claims and whether the data they threaten to leak belongs to MSI remain unverified.

Malware
USDoD Hacker Responsible for Massive National Public Data Breach Captured in Brazil
Brazilian authorities have arrested a hacker accused of stealing 223GB of sensitive data from the US Department of Defense (DoD). The hacker, known as “Zambrius,” sold the data on the dark web and was also involved in other cybercrimes.

Imagine waking up one day to find your personal information plastered all over the internet. Well, that nightmare became a reality for millions of Americans when notorious hacker USDoD, also known as EquationCorp, breached National Public Data and the FBI’s InfraGard, leaking sensitive information online. But this cybercriminal’s reign of terror has come to an end, as Brazil’s Polícia Federal recently arrested USDoD in “Operation Data Breach.”
USDoD’s Infamous Data Breaches
USDoD gained notoriety for his high-profile data breaches, often stealing data and leaking it on hacking forums while taunting his victims. His breaches include the FBI’s InfraGard, a threat information sharing portal, and National Public Data, where the personal data and social security numbers of hundreds of millions of US citizens were leaked online.
However, things took a turn for the worse for USDoD when he targeted cybersecurity firm CrowdStrike and leaked the company’s internal threat actor list.
How USDoD Was Caught
After leaking CrowdStrike’s list, Brazilian publisher Techmundo received an anonymous report created by CrowdStrike that allegedly identified, or doxed, the threat actor, revealing he was a 33-year-old Brazilian named Luan BG. Strangely, USDoD confirmed that CrowdStrike’s information was accurate in an interview with HackRead and said he was currently living in Brazil.
With this information, Brazil’s Polícia Federal (PF) announced his arrest in Belo Horizonte/MG. “The Federal Police launched Operation Data Breach on Wednesday (16/10), with the aim of investigating invasions of the systems of the Federal Police and other international institutions,” reads the PF’s press release.
The Importance of Cybersecurity
This arrest serves as a reminder of the importance of cybersecurity. As individuals and businesses, we must stay vigilant and proactive in protecting our sensitive data. But you don’t have to navigate the world of cybersecurity alone.
Our IT Services team is here to help you protect your data and ensure your digital safety. From implementing robust security measures to providing guidance on best practices, we’ll work with you to keep your information secure.
Stay Informed and Stay Safe
Knowledge is power, and staying informed about the latest cybersecurity threats and best practices is the first step in keeping your data safe. We encourage you to reach out to our team and keep coming back to learn more about how to protect yourself and your business from cybercriminals.
Malware
Cisco Probes Intrusion as Stolen Data Emerges for Sale on Cybercriminal Platform
Cisco is investigating a potential breach after a hacker claimed to have stolen 200GB of sensitive data. The company is working to determine the authenticity of the claim and assess any potential impacts on its customers. Protect your network with Cisco’s integrated security solutions and stay informed with the latest cybersecurity updates.

Recently, we received information that Cisco, a leading IT company, is investigating a possible data breach after a threat actor claimed to have stolen sensitive data and put it up for sale on a hacking forum. Don’t worry, we’ve got you covered with the latest updates on this situation.
What’s going on with Cisco?
Cisco confirmed that they are looking into these claims and have launched an investigation to assess the situation. A Cisco spokesperson stated, “We are aware of reports that an actor is alleging to have gained access to certain Cisco-related files.” The investigation is still ongoing.
This all started when a notorious threat actor going by the name “IntelBroker” claimed that they, along with two accomplices called “EnergyWeaponUser” and “zjj,” had breached Cisco on October 6, 2024, and made off with a significant amount of developer data from the company. The stolen data apparently includes GitHub projects, GitLab projects, SonarQube projects, source code, hardcoded credentials, customer documents, and much more.
What has been leaked?
IntelBroker shared samples of the alleged stolen data, which includes a database, customer information, various customer documentation, and screenshots of customer management portals. However, they did not provide any details about how they obtained the data.
It’s worth noting that back in June, IntelBroker was involved in selling or leaking data from several other companies, such as T-Mobile, AMD, and Apple. Those attacks were believed to have been carried out by targeting a third-party managed services provider for DevOps and software development. It’s not clear yet whether the Cisco breach is related to these previous incidents.
What’s the current status of the investigation?
As of now, Cisco is continuing to investigate the reports and has engaged law enforcement to assist in their efforts. So far, they have found no evidence of a breach in their systems. If any confidential customer information is confirmed to have been obtained by the threat actor, Cisco has stated that they will notify the affected customers.
In conclusion, it’s essential to stay vigilant and keep up-to-date on the latest cybersecurity news and threats. You can trust us to provide you with the most recent information and help you navigate the ever-evolving world of cybersecurity. Don’t hesitate to contact us to learn more about how to protect your organization, and keep coming back for more updates on this and other cybersecurity topics.
Malware
Game Freak Confirms Massive Breach: Stolen Pokémon Data Exposed Online
Game Freak, the developer behind Pokémon, has confirmed a security breach after stolen data leaked online. The leaked data includes information on unreleased games, potentially impacting both the company and fans. Game Freak is working to address the situation and strengthen their security measures to prevent future incidents.

Imagine spending years of your life working on a top-secret project, only for it to be stolen and leaked online. That’s what happened to Game Freak, the Japanese video game developer behind the wildly popular Pokémon series, in August 2024. And now, we’re learning just how extensive the damage was.
A Digital Heist in the World of Pokémon
Game Freak has been at the forefront of the Pokémon gaming world since 1996, when they released Pokémon Red and Blue for the Nintendo Game Boy. Since then, they’ve produced countless titles for various Nintendo platforms, as well as for iOS and Android devices.
But in August, things took a turn for the worse. Screenshots of source code and development builds for upcoming Pokémon games started appearing on leak sites and channels like Discord, Reddit, and X. While Game Freak didn’t acknowledge the leak of the game data, they did confirm something even more concerning: the personal information of their workforce, contractors, and former employees was stolen in the cyberattack.
Damage Control and Apologies
In a machine-translated notice, Game Freak stated, “We deeply apologize for any inconvenience and concern this may have caused to all concerned parties.” They went on to explain that the leaked information included full names and company email addresses. While this doesn’t put people at risk for identity theft, it does leave them vulnerable to phishing and targeted brute-forcing attacks.
Game Freak is working to contact those affected by the incident individually, but they published the notice on their site because not everyone can be reached. On a positive note, it seems that Pokémon player data hasn’t been impacted. Game Freak has completed a detailed investigation of the breached servers and implemented security measures to prevent similar incidents in the future.
Not an Isolated Incident
Game Freak isn’t the only gaming company to fall victim to a cyberattack recently. Earlier this month, Canadian video game developer Red Barrels warned its community that an attack could cause delays on patches and additional content for existing Outlast games and upcoming titles. The Nitrogen ransomware group later claimed responsibility for the attack, boasting that they had stolen 1.8 TB of confidential data from Red Barrels.
As for the attack on Game Freak, no one has claimed responsibility yet. But the fact remains that this is a stark reminder of the vulnerability of even the most successful companies in the gaming industry.
What You Can Do to Help
As fans and consumers, it’s essential for us to stay informed and vigilant about cybersecurity. By keeping up-to-date with the latest news and best practices, we can help protect ourselves and the companies we love from these devastating cyberattacks.
But you don’t have to do it alone. Our IT Services team is here to help you navigate the ever-evolving landscape of cybersecurity. Don’t hesitate to contact us with any questions or concerns you might have. And remember to keep coming back for the latest information and advice on staying secure in the digital world.
-

 Malware1 year ago
Malware1 year agoFlagstar Bank’s Latest Data Breach: 800,000 Customers Impacted, Marking the Third Incident of 2021
-

 Malware1 year ago
Malware1 year agoBlackbaud: Taking Responsibility with a Landmark $49.5 Million Settlement for Devastating Ransomware Data Breach
-

 Data Protection Regulations11 months ago
Data Protection Regulations11 months agoTop Data Protection Officer Certification Courses Reviewed
-

 Data Protection Regulations11 months ago
Data Protection Regulations11 months agoTop 11 Data Protection Training Programs for Compliance
-

 Security Audits and Assessments11 months ago
Security Audits and Assessments11 months agoMastering Healthcare Data Security: 5 Essential Audit Tips
-

 Data Protection Regulations11 months ago
Data Protection Regulations11 months agoNavigating Data Protection Laws for Nonprofits
-

 Data Protection Regulations11 months ago
Data Protection Regulations11 months ago9 Best Insights: CCPA’s Influence on Data Security
-

 Security Audits and Assessments11 months ago
Security Audits and Assessments11 months agoHIPAA Security Risk Assessment: Essential Steps Checklist






















