Malware
Exclusive Access to Sought-After BreachForums Database and Private Chats Now Available in Thrilling Hacker Data Breach Auction
Breachforums, a notorious hacker forum, has fallen victim to a major data breach. The attackers have gained access to the platform’s database and private chats, compromising sensitive information. This breach raises concerns about the security of user data and highlights the growing risks of online platforms. Find out more about this alarming incident and its implications.

Breached Cybercrime Forum’s Database for Sale and Shared with Have I Been Pwned
Concerns about data breaches usually revolve around consumers and their exposed information. However, it is now the hackers who are feeling the heat as the notorious Breached cybercrime forum’s database is up for sale and its member data has been shared with Have I Been Pwned.
Yesterday, the data breach notification service Have I Been Pwned announced that visitors can check if their information was compromised in a data breach of the Breached cybercrime forum.
“In November 2022, the well-known hacking forum “BreachForums” was itself breached. Later the following year, law enforcement agencies arrested the operator of the website and seized the site,” reads the announcement from Have I Been Pwned.
The breach exposed 212k records, including usernames, IP and email addresses, private messages between site members, and passwords stored as argon2 hashes.
Breached was a large hacking and data leak forum notorious for hosting, leaking, and selling data stolen from hacked companies, governments, and organizations worldwide.
After the arrest of the site’s admin Pompompurin in March 2023, the remaining administrator, Baphomet, decided to shut down the forum due to concerns that law enforcement also had access to the site’s servers.
Subsequently, Baphomet launched a new version of the forum called BFv2 with another data breach seller known as Shiny Hunters.
Did the Ransomware Attack on the Parent Company of KFC and Pizza Hut Lead to the Data Breach?
The recent ransomware attack on the kfc and pizza hut parent company has raised concerns about a potential data breach. As cybercriminals exploit vulnerabilities, it remains uncertain if sensitive data from these popular restaurant chains has been compromised. Investigations are underway to determine the extent of the breach and safeguard customer information.
A Valuable Data Source
The Breached database is currently being sold by a threat actor known as “breached_db_person.” They have shared the database with Have I Been Pwned to validate its authenticity for potential buyers.
BleepingComputer has also verified that known Breached accounts are listed in the shared member’s table.
Previous Breached admin Baphomet has confirmed the legitimacy of the database and issued a warning that its sale is part of an ongoing campaign to dismantle the community.
“Not only was the database submitted to Have I Been Pwned, but it is also being actively sold and leaked by at least one person, who even attempted to do so on our forum,” warned Baphomet.
“For that reason, I’m sure we’re going to see it become public soon enough. Judging by the 212k users, this is likely an older database from months before the closure of BFv1, considering that my last forum backup had 336k users.”
According to the seller, only law enforcement, Baphomet, and Pompompurin possess the database.
The threat actor is offering to sell the Breached database to a single buyer for $100,000 – $150,000. The database contains a snapshot of the entire dataset taken on November 29th, 2022.
The database is approximately 2 GB in size and includes all tables, such as private messages, payment transactions, and the member database.
Source: BleepingComputer
While the FBI has already gained access to the Breached database after seizing the servers, this data remains valuable for cybersecurity researchers and potentially other threat actors.
The seller, breached_db_person, informed BleepingComputer that the private message tables contain incriminating information about forum members. Furthermore, the “members” database includes IP addresses, indicating that many threat actors do not employ good operational security and instead use residential IP addresses.
The private messages table holds great value as it contains messages exchanged privately among forum members, potentially revealing information about past attacks, identities, and other useful details.
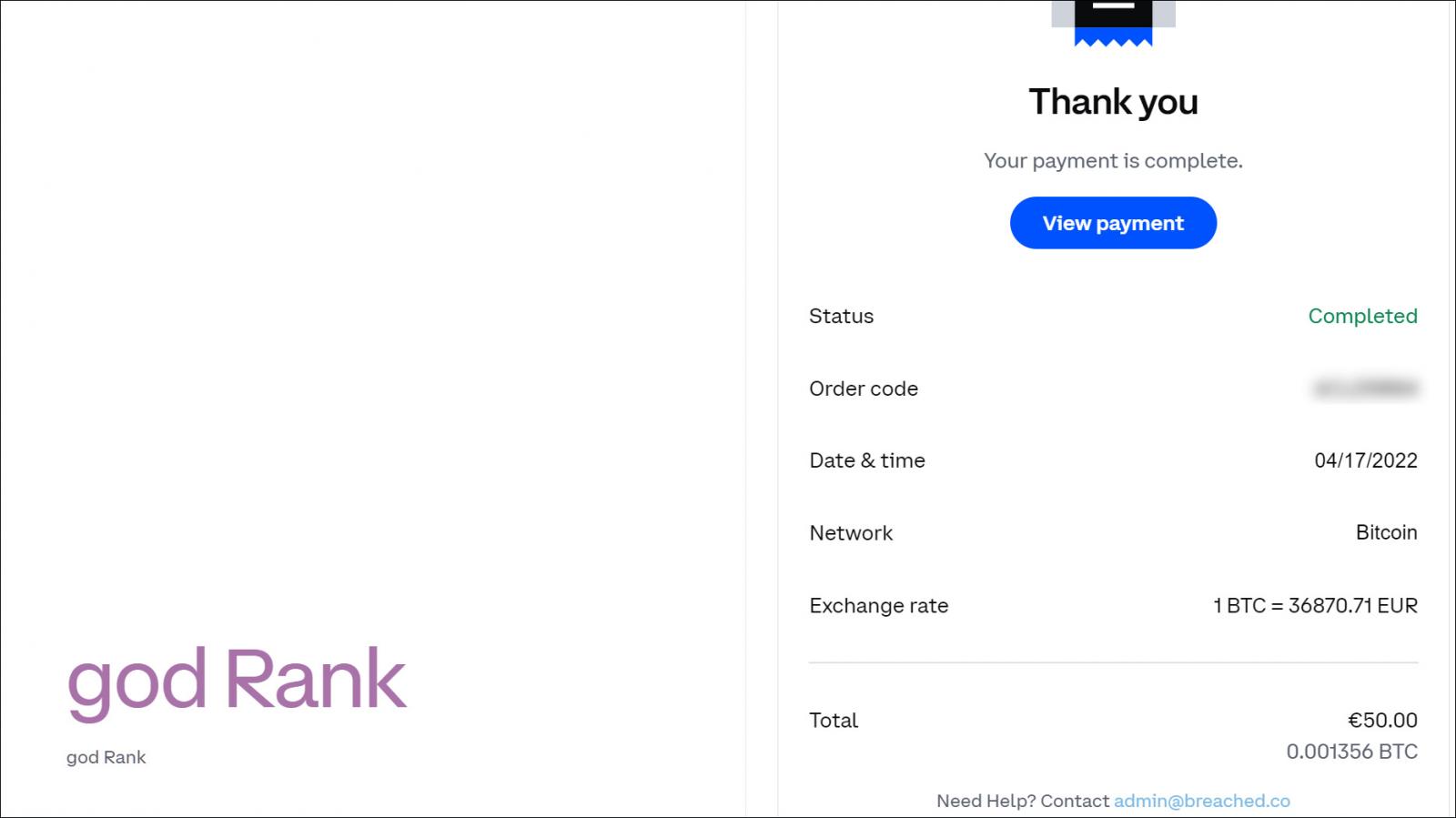
Samples from the payments table were shared with BleepingComputer and contain information about payments made to purchase forum ranks (membership levels with additional benefits) and credits (a form of forum currency).
These payments were processed through CoinBase Commerce or Sellix, with Coinbase transactions including links to order confirmations that may contain sensitive information, such as cryptocurrency addresses and Coinbase payment IDs.
This cryptocurrency data can be valuable to blockchain analytics companies, allowing them to link threat actors to criminal activities using the cryptocurrency addresses.
Source: BleepingComputer
Breached and its members have been responsible for numerous hacks, extortion attempts, ransomware attacks, and the leaking of stolen data from various companies. These breaches include DC Health Link, Twitter, RobinHood, Acer, Activision, and many others.
Therefore, the private messages could prove invaluable to researchers. The seller mentioned that they have already been contacted by cybersecurity firms requesting a copy of the data for their own research.
Other threat actors have also expressed interest, with one offering $250,000 for the database.
Although it is still too early to determine whether the database will be sold, even if it is, it would not be surprising for the entire dataset to be leaked for free in the future.
It is common for data breaches to initially be privately purchased and then released later to enhance reputation within the data theft community.
Recently, the seized RaidForums data breach forum also experienced a data breach, and the new BreachedForums clone (BFv2) had its database leaked.
Malware
Dell Sounds Alarm on Massive Data Breach: 49 Million Customers Potentially Impacted
Dell has warned 49 million customers of a potential data breach as unauthorized individuals attempted to extract customer data from its network. The company has reset all affected users’ passwords and is urging them to stay vigilant for any suspicious activity.

Did you know that Dell recently experienced a data breach? A threat actor claimed to have stolen information for approximately 49 million customers. As a result, Dell started sending out data breach notifications to customers, informing them that a Dell portal containing customer information related to purchases was breached.
Now, you might be wondering, what kind of information was accessed during this breach? Well, according to Dell, the following information was compromised:
- Name
- Physical address
- Dell hardware and order information, including service tag, item description, date of order, and related warranty information
Fortunately, the stolen information does not include financial or payment information, email addresses, or telephone numbers. Dell is currently working with law enforcement and a third-party forensics firm to investigate the incident.
How did this happen?
As reported by Daily Dark Web, a threat actor named Menelik tried to sell a Dell database on the Breach Forums hacking forum on April 28th. The threat actor claimed to have stolen data from Dell for “49 million customers and other information systems purchased from Dell between 2017-2024.” While we haven’t been able to confirm if this is the same data that Dell disclosed, it matches the information listed in the data breach notification.
The post on Breach Forums has since been deleted, which could indicate that another threat actor purchased the database.
What does this mean for Dell customers?
Although Dell doesn’t believe there is significant risk to its customers given the type of information involved, the stolen information could potentially be used in targeted attacks against Dell customers. Without email addresses, threat actors might resort to targeting specific people with physical mailings containing phishing links or media (DVDs/thumb drives) to install malware on targets’ devices.
Think this sounds far-fetched? Well, similar attacks have happened in the past. For instance, tampered Ledger hardware wallets were physically mailed, which then stole cryptocurrency, or gifts with USB drives were sent that installed malware.
Since the database is no longer being sold, there’s a good chance a threat actor is trying to monetize it in some way through attacks. So, what can you do to protect yourself?
Stay vigilant and be cautious
Be wary of any physical mailings or emails you receive that claim to be from Dell, asking you to install software, change passwords, or perform some other potentially risky action. If you receive any suspicious communication, contact Dell directly to confirm its legitimacy.
Remember, knowledge is power, and staying informed about cybersecurity threats is essential to protecting yourself and your information. Don’t hesitate to contact us for more information and resources on cybersecurity, and keep coming back to learn more.
Malware
800K Users Compromised: The Alarming 2023 MOVEit Cyberattack Unleashed
Learn how the University System of Georgia suffered a massive data breach in 2023, exposing the personal information of over 800,000 individuals. Discover the role of the Moveit attack and its impact on cybersecurity in the education sector. Stay informed on the latest data protection measures to keep your information safe.

Imagine waking up one day to find out your personal information, including your Social Security number and bank account details, has been stolen by cybercriminals. This is what happened to 800,000 individuals when the University System of Georgia (USG) fell victim to the notorious Clop ransomware gang in 2023.
USG, a state government agency responsible for operating 26 public colleges and universities in Georgia, was among the first to be compromised in a massive worldwide data theft campaign conducted by the Clop gang. They exploited a zero-day vulnerability in the Progress Software MOVEit Secure File Transfer solution, impacting thousands of organizations around the globe.
How the breach unfolded
With the help of the FBI and CISA, USG eventually determined that sensitive files had been stolen from its systems. Almost a year later, they began notifying the impacted individuals, revealing that the cybercriminals accessed the following information:
- Full or partial (last four digits) of Social Security Number
- Date of Birth
- Bank account number(s)
- Federal income tax documents with Tax ID number
Considering the type of information exposed and the fact that the number of impacted individuals is larger than the number of students under USG, it’s likely that prior students, academic staff, contractors, and other personnel were also affected.
USG submitted a sample of the data breach notice to the Office of the Maine Attorney General, stating that the data breach impacts 800,000 people. Interestingly, the entry on Maine’s portal also lists driver’s license numbers or identification card numbers as exposed data types, although these are not mentioned in the notice.
What’s being done to help the victims?
To help those affected, USG is now offering 12 months of identity protection and fraud detection services through Experian. Impacted individuals have until July 31, 2024, to enroll in these services.
Unfortunately, the MOVEit attacks by Clop were one of the most successful and prolific extortion operations in recent history. Over a year after the attacks took place, organizations are still discovering, confirming, and disclosing breaches, extending the aftermath of the cyber-attacks.
Emsisoft’s dedicated counter of MOVEit victims lists 2,771 impacted organizations and nearly 95 million individuals whose personal data now resides in Clop’s servers. Some of that data was published on Clop’s extortion portal on the dark web, some were sold to other cybercrime groups, and some remain to be monetized in the future.
What can you do to protect yourself?
This data breach serves as a stark reminder of the importance of cybersecurity and vigilance in our increasingly digital world. Organizations and individuals must prioritize cybersecurity measures, such as using strong, unique passwords, enabling multi-factor authentication, and regularly updating software and systems.
For more information on how to protect yourself and your organization from cyber threats, don’t hesitate to contact us. Our team at IT Services is dedicated to helping you stay safe in this ever-evolving digital landscape. Keep checking back for more insights and advice on cybersecurity!
Malware
DocGo Reveals Devastating Cyberattack: Hackers Breach and Steal Crucial Patient Health Data
Medical transportation company DocGo disclosed a cyberattack that led to unauthorized access of patients’ health data. The company has taken steps to enhance security measures and is working with cybersecurity experts to investigate the incident, emphasizing the importance of safeguarding sensitive information and preventing future breaches.

Imagine this: you’re at home, recovering from a recent surgery, when suddenly you receive a letter from your healthcare provider. They inform you that your personal health information has been compromised due to a cyberattack. This nightmare scenario recently became a reality for some patients of mobile medical care firm, DocGo.
DocGo’s Cybersecurity Breach: What Happened?
DocGo is a healthcare provider offering mobile health services, ambulance services, and remote monitoring for patients in 30 US states and across the United Kingdom. In a recent filing with the SEC, DocGo confirmed that it had suffered a cyberattack when threat actors breached its systems and stole patient health data.
Upon detecting unauthorized activity, DocGo promptly took steps to contain and respond to the incident. They launched an investigation with the assistance of leading third-party cybersecurity experts and notified relevant law enforcement.
The Aftermath: How DocGo Responded
Although DocGo did not share specifics about how they responded to the incident, organizations typically shut down their IT systems after detecting a breach to prevent the attack from spreading. As part of DocGo’s investigation, it was determined that the hackers stole protected health information from a “limited number of healthcare records” for the company’s US-based ambulance transportation business.
DocGo is now actively reaching out to individuals whose data was compromised in the attack. They stress that no other business units have been affected, and they have found no evidence of continued unauthorized access. Additionally, DocGo does not believe that the attack will have a material impact on the company’s operations and finances.
Who’s Responsible and What’s Next?
No threat actors have claimed responsibility for the breach. However, if it was a ransomware attack and a ransom is not paid, it’s likely that the stolen data will be used as leverage in the future to extort DocGo. We contacted DocGo to learn how many people were affected by the breach, but a reply was not immediately available.
Stay Informed, Stay Protected
This recent cyberattack on DocGo is a stark reminder of the importance of cybersecurity – not just for businesses, but for individuals as well. As personal information becomes more interconnected and accessible through technology, it’s crucial to stay informed about potential threats and take necessary precautions to safeguard your data.
If you want to learn more about cybersecurity and how to protect yourself and your information, don’t hesitate to contact our IT Services team for expert advice and assistance. And remember – knowledge is power. Keep coming back to stay informed and stay protected.
-

 Malware7 months ago
Malware7 months agoFlagstar Bank’s Latest Data Breach: 800,000 Customers Impacted, Marking the Third Incident of 2021
-

 Malware7 months ago
Malware7 months agoBlackbaud: Taking Responsibility with a Landmark $49.5 Million Settlement for Devastating Ransomware Data Breach
-

 Data Protection Regulations6 months ago
Data Protection Regulations6 months agoTop Data Protection Officer Certification Courses Reviewed
-

 Security Audits and Assessments6 months ago
Security Audits and Assessments6 months agoMastering Healthcare Data Security: 5 Essential Audit Tips
-

 Data Protection Regulations6 months ago
Data Protection Regulations6 months agoTop 11 Data Protection Training Programs for Compliance
-

 Security Audits and Assessments6 months ago
Security Audits and Assessments6 months agoHIPAA Security Risk Assessment: Essential Steps Checklist
-

 Data Protection Regulations6 months ago
Data Protection Regulations6 months ago9 Best Insights: CCPA’s Influence on Data Security
-

 Data Protection Regulations6 months ago
Data Protection Regulations6 months agoNavigating Data Protection Laws for Nonprofits



















